About Dream Market: Official Info & Main Platform Guide
Looking for real info about Dream Market? You're in the right place. This page covers everything you need to know: platform features, security setup, how vendors get verified, and which cryptocurrencies work. No fluff. Just facts.
Dream Market Platform Overview
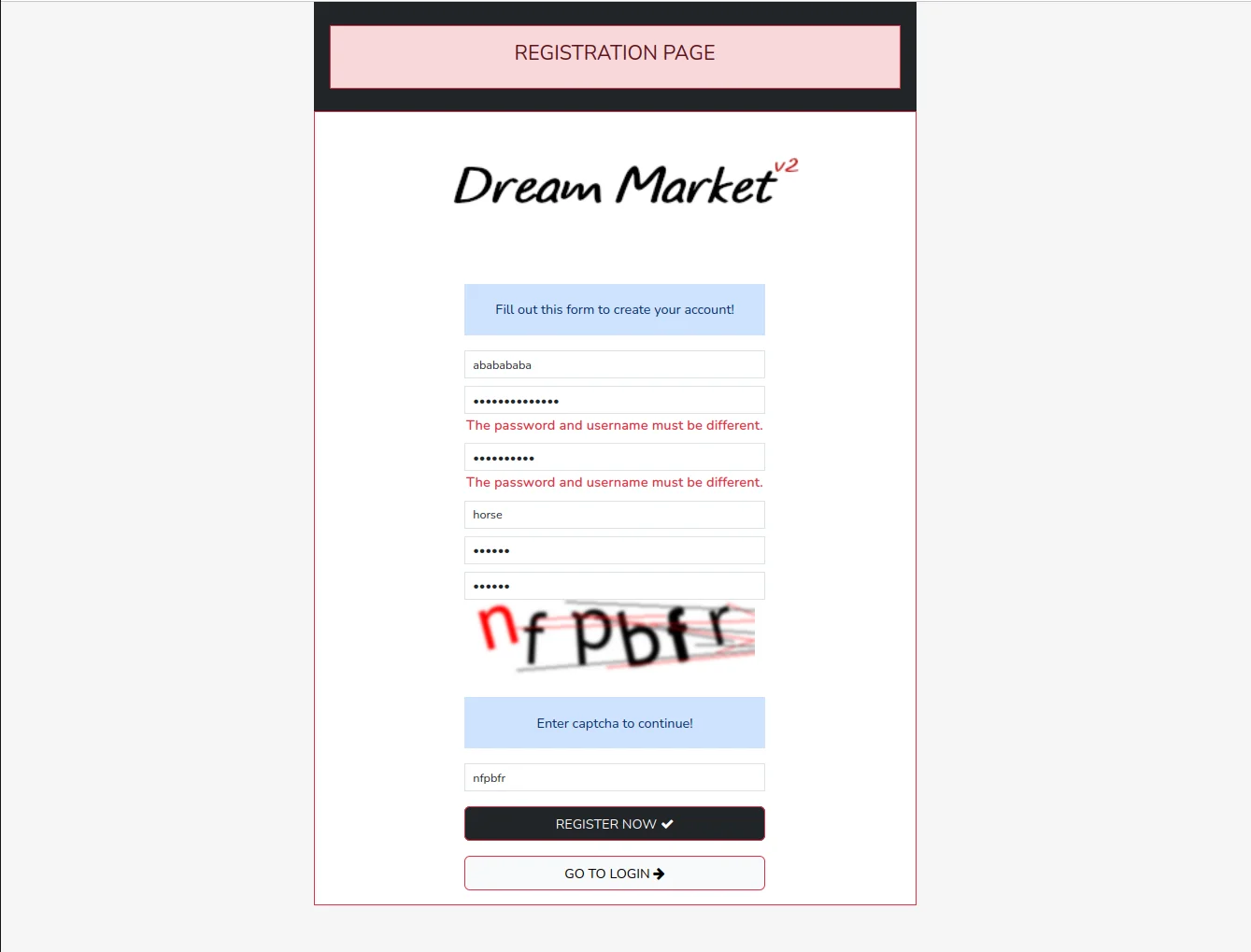
Dream Market launched in 2013. Still running. That alone tells you something - most platforms don't last a year. This one's been around for over a decade, processing thousands of orders daily while competitors came and went.
What makes it work? Simple philosophy: security first, everything else second. The platform connects buyers with verified vendors across dozens of categories. Privacy-focused users keep coming back because the system actually delivers what it promises.
Historical Background
The platform emerged during a transformative period for anonymous marketplaces. Founders studied what killed previous platforms and built accordingly. Strong security from day one. No shortcuts.
Evolution never stopped. Community feedback drives updates. Security threats get addressed fast. That's why this marketplace survived while dozens of others failed. Adaptation matters more than promises.
Core Mission and Values
What does the platform actually prioritize? Here's the short list:
- Security: Multiple protection layers for everyone involved
- Fair Transactions: Escrow ensures both sides get what they agreed to
- Real Privacy: Technical safeguards, not just policies
- Trust: Transparent rules, consistent enforcement
- Uptime: Multiple mirrors, accessible infrastructure
- Vendor Accountability: Verification systems that actually work
- User Support: Real responses to real problems
- Continuous Improvement: Regular updates based on user needs
Dream Market Main Features & Capabilities
What sets this platform apart? Advanced encryption, multi-sig escrow, vendor verification, and solid cryptocurrency support. Let's break each one down.
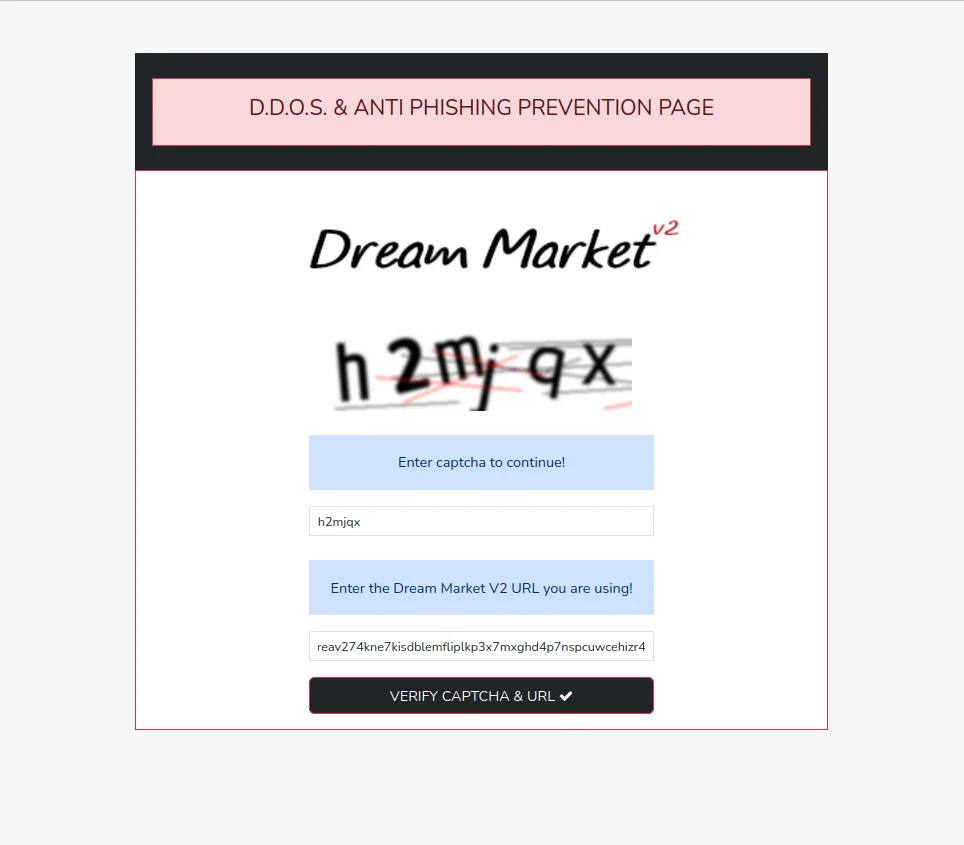
Mandatory PGP Encryption
4096-bit PGP encryption. Not optional. Every communication gets encrypted automatically. Even if servers get compromised, your sensitive data stays protected. Here's how it works:
- Server-side automatic encryption - no plaintext storage ever
- PGP key verification confirms message authenticity
- End-to-end protection for all buyer-vendor messages
- Encrypted address transmission keeps shipping info safe
- PGP-based 2FA for account access
- Key rotation options for enhanced security
- Automatic message expiration settings
- Encrypted backup options for important data
Multi-Signature Escrow System
How do you prevent theft? 2-of-3 multi-signature technology. Three parties involved: buyer, vendor, platform. Any transaction needs two signatures to release funds. Nobody can run off with money unilaterally.
- Standard Escrow: Funds held until buyer confirms receipt
- Auto-Finalize: Automatic release after set period (configurable)
- Dispute Resolution: Arbitrators handle contested transactions
- Partial Refunds: Damaged item? Get partial money back
Vendor Verification Process
Not everyone can sell here. Quality control starts with verification: bond deposits, identity checks within the platform, probationary periods. Four vendor tiers exist:
- New Vendors: Initial bond required, limited listings allowed
- Established: More features unlock after proven track record
- Trusted: Highest tier for vendors with extensive positive history
- FE-Approved: Finalize-early privileges for exceptional sellers only
Dream Market Security Architecture
Security isn't optional here. It's enforced at every level. Defense-in-depth strategy means multiple protection layers - if one fails, others catch the threat.
Infrastructure Security
Technical architecture designed to resist attacks and avoid single points of failure:
- Distributed Servers: Multiple jurisdictions, no central target
- DDoS Protection: Advanced traffic filtering plus mirror network
- Database Encryption: All stored data encrypted at rest
- Hardware Security Modules: Critical operations protected by HSMs
- Penetration Testing: Regular security audits by external teams
- Zero-Knowledge Architecture: Minimal data retention policies
- Automated Threat Detection: Real-time monitoring systems
- Redundant Backups: Encrypted, distributed, recoverable
Account Security
Your account gets multiple protection layers. Not one. Multiple.
- PGP-Based 2FA: Required for sensitive actions
- Login Monitoring: Suspicious attempts trigger alerts
- Session Management: Inactive sessions expire automatically
- Withdrawal PIN: Separate code for crypto withdrawals
- Account Recovery: PGP-based secure recovery process
- Login History: Full access log for your review
- Device Fingerprinting: Unusual devices flagged
- Forced Logout: Remote session termination option
- Password Requirements: Strong passphrase enforcement
Operational Transparency
How do you know the platform hasn't been compromised? Transparency mechanisms:
- Warrant Canary: Cryptographically signed statements published regularly
- System Status: Real-time mirror status visible to all
- Policy Updates: Changes announced with advance notice
- Incident Disclosure: Security issues affecting users get reported
Dream Market Cryptocurrency Integration
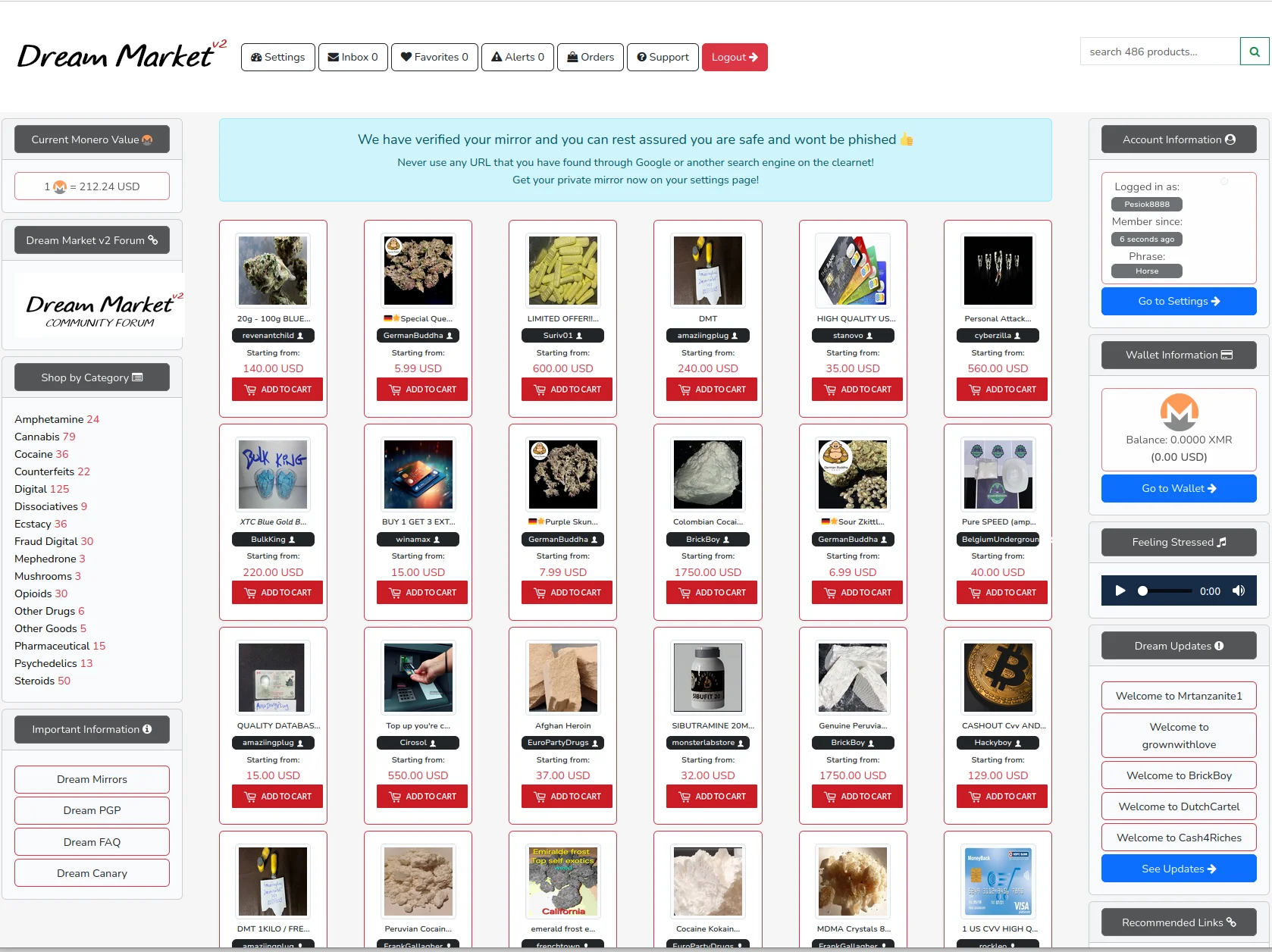
Two cryptocurrencies supported: Bitcoin and Monero. Platform increasingly recommends XMR for better privacy. Here's why both options exist.
Bitcoin Support
The original cryptocurrency. Full support includes:
- Complete deposit and withdrawal functionality
- HD wallet - unique address for each deposit
- 2-3 confirmations required (standard security)
- Fee options for priority processing
- SegWit addresses supported for lower fees
- Real-time BTC/USD conversion display
- Transaction history export
- Address book for frequent withdrawals
Monero - The Privacy Choice
Want real financial privacy? XMR is the answer. Blockchain analysis? Impossible with Monero.
- Native wallet integration built-in
- Zero blockchain traceability
- Lower fees than Bitcoin
- Direct BTC-to-XMR conversion available
- Faster confirmation times
- Ring signatures hide transaction origins
- Stealth addresses for receiving
- RingCT hides transaction amounts
- No rich list - balances invisible
Wallet Security Architecture
"Walletless" design minimizes stored crypto. Less stored = less to steal.
- Escrow holds funds during transactions
- Minimal hot wallet exposure
- Cold storage for reserves
- Multi-sig withdrawal authorization
Dream Market User Experience
Security matters. But so does usability. A platform nobody can figure out is useless. That's why the interface balances both concerns.
Interface Design
Clean. Functional. No clutter.
- Clean Layout: Information presented without visual noise
- Logical Navigation: Categories organized intuitively
- Mobile Support: Works on Tor Browser for Android
- Accessibility: High-contrast and simplified modes available
- Fast Loading: Optimized for Tor network speeds
- Keyboard Navigation: Full site accessible without mouse
- Consistent Styling: Same patterns across all pages
- Clear CTAs: Obvious action buttons
- Error Messages: Helpful, not cryptic
Search and Discovery
Finding what you need shouldn't take forever. Search features include:
- Full-text search across all listings
- Category and subcategory filtering
- Price range sliders
- Shipping destination filters
- Vendor rating filters
- Saved searches and watchlists
- Recently viewed items
- Similar product suggestions
Communication Tools
Buyer-vendor messaging. Secure by default.
- Automatic PGP encryption on all messages
- Order-linked conversations maintain context
- Dispute submission through messaging
- Vendor announcements and updates
Dream Market Support & Community
Problems happen. When they do, support channels exist. Active community engagement too.
Customer Support
- Ticket System: Structured request handling
- Response Times: 24-48 hours typical
- Dispute Mediation: Professional arbitration available
- Account Recovery: Help with locked accounts
- Priority Support: Faster response for verified vendors
- Multilingual: Support in multiple languages
- FAQ Database: Common issues documented
- Tutorial Library: Step-by-step guides
- Status Updates: Ticket progress visible
Community Resources
- Official forum for discussions
- Vendor verification announcements
- Security advisories and updates
- Feature request system
- Community voting on proposals
- Vendor spotlight features
- Buyer guides and tips
- Security awareness content
Trust and Safety
Beyond support tickets - proactive trust and safety measures:
- Scam vendor detection and removal
- Phishing link warnings
- Buyer protection programs
- Vendor feedback verification
Privacy Philosophy & Principles
Why does privacy matter online? Because every transaction you make, every site you visit, every message you send creates a data trail. Governments, corporations, hackers - all interested in that data. Anonymous platforms exist because privacy is a fundamental right, not a criminal tool.
The Case for Anonymity
Consider who benefits from anonymous transactions:
- Journalists protecting sources in authoritarian regimes
- Activists organizing under oppressive governments
- Whistleblowers exposing corporate wrongdoing
- Citizens in countries with currency controls
- People escaping domestic abuse situations
- Anyone who believes their financial data is private
- Security researchers studying darknet ecosystems
- Privacy advocates testing anonymity tools
- Individuals in professions requiring discretion
Technical Privacy Layers
True privacy requires multiple technical layers working together. No single technology provides complete protection. That's why the platform combines:
- Tor Network: Onion routing hides your IP address from destination servers
- PGP Encryption: End-to-end protection ensures only intended recipients read messages
- Cryptocurrency: Bitcoin provides pseudonymity, Monero provides true anonymity
- Metadata Minimization: Less data collected means less data to leak
- Zero-Knowledge Design: Systems designed so operators can't access user data
- Forward Secrecy: Compromised keys don't decrypt past communications
- Plausible Deniability: Hidden volumes and steganography options
- Secure Deletion: Data that doesn't exist can't be seized
Privacy vs Security Trade-offs
Perfect privacy and perfect security sometimes conflict. Understand the trade-offs:
- Stronger encryption means slower performance
- More anonymity makes support harder
- No logs means no audit trail for disputes
- Decentralization increases complexity
Each user must decide their own balance. The platform provides tools. You decide how to use them.
Platform Development & Roadmap
Platforms that don't evolve die. Continuous development keeps the system relevant and secure. Here's what development looks like:
Recent Improvements
- Enhanced DDoS protection with additional mirror infrastructure
- Improved mobile compatibility for Tor Browser users
- Faster search with optimized database queries
- Streamlined dispute resolution process
- Better cryptocurrency price feeds
- Updated PGP verification workflow
- New vendor analytics dashboard
- Improved notification system
Ongoing Focus Areas
- Security Hardening: Regular audits and penetration testing
- Performance: Faster load times over Tor
- UX Refinement: Cleaner interfaces, better workflows
- Cryptocurrency Support: Keeping up with blockchain developments
- Anti-Phishing: Protecting users from fake sites
- Documentation: Better guides and tutorials
- Community Features: Forums, feedback systems
- Vendor Tools: Better inventory and order management
- Buyer Protection: Enhanced escrow and dispute systems
Community-Driven Development
Users drive improvements. Feature requests get reviewed. Bug reports get addressed. The best platforms listen to their communities. Feedback channels:
- Support ticket suggestions
- Forum discussions
- Vendor feedback programs
- Security researcher bounties
Best Practices for Anonymous Trading
Knowledge is protection. Understanding how to use anonymous systems properly separates successful users from those who get burned. Follow these principles:
Before You Start
- Research thoroughly before transacting with anyone
- Set up your security tools properly - Tor, PGP, encrypted storage
- Never reuse usernames or passwords across platforms
- Create dedicated email addresses with no ties to real identity
- Practice with small amounts first to learn the system
- Read reviews carefully - patterns matter more than individual ratings
- Understand cryptocurrency basics before depositing funds
- Bookmark official links using PGP-signed sources only
- Learn to recognize phishing attempts and fake sites
During Transactions
- Always encrypt sensitive information with PGP
- Never share more information than necessary
- Use escrow for every transaction - no exceptions
- Document everything in case of disputes
- Communicate only through platform messaging systems
- Verify vendor PGP keys before sending encrypted data
- Check order details carefully before confirming
- Keep records of transaction IDs and timestamps
After Transactions
- Leave honest reviews to help other buyers
- Report problems promptly through proper channels
- Clear browser data and rotate Tor circuits regularly
- Don't leave funds sitting on platforms unnecessarily
- Update security tools when new versions release
- Stay informed about platform status and announcements
Red Flags to Watch
Warning signs that something might be wrong:
- Vendors asking you to finalize early without reputation
- Unusual payment requests outside normal channels
- Pressure to act quickly without time to research
- Links from unverified sources claiming to be official
- Requests for personal information beyond shipping needs
- Prices significantly below what competitors charge
- Newly created accounts with no transaction history
- Poor communication or evasive answers to questions
Trust develops through consistent behavior over time. Quick trust rarely ends well. Patience protects you. Watch patterns rather than individual incidents. Multiple small warning signs often matter more than one obvious red flag. When something feels wrong, it usually is.
Access Links
View verified mirrors and official onion URLs with real-time status monitoring.
Access Page →Security Guides
Learn essential security practices for safe usage including PGP and OPSEC tutorials.
Security Center →User Guides
Step-by-step tutorials for registration, purchasing, and vendor operations.
View Guides →🕒 Page last updated: