Dream Market Access: Official Links, Mirrors & Onion URLs
Looking for verified access links? You're in the right place. This page provides current mirrors, onion URLs with real-time status, and everything you need to connect safely. Step-by-step instructions included. PGP verification methods explained.
⚠️ Critical Security Notice
Before accessing any darknet platform through links or mirrors, understand the security requirements. Proper measures protect your anonymity and prevent credential theft. Follow these guidelines:
- Tor Browser Required: Onion links only work through Tor Browser - never use regular browsers
- Verify PGP Signatures: Always check links against official PGP-signed mirror lists before entering credentials
- Check URL Format: V3 onion addresses have 56 characters - reject any shorter URLs
- Bookmark Verified Links: Save verified mirrors in Tor Browser bookmarks to avoid phishing
- Enable 2FA: Activate PGP-based two-factor authentication on your account
- Never Trust Search Engines: Don't search for onion links - use only verified sources like this page
- Check Mirror Status: Verify real-time status before attempting connection
- Use Fresh Circuits: Request new Tor circuit if connection seems compromised
- No Personal Info: Never enter real identity information anywhere
Access Information
🔒 Viewing Links
To view current links and mirrors with real-time status:
- Return to the Wiki homepage and review security information
- Navigate back to this access page
- Current mirrors will be displayed with online/offline status
What's Available on This Page:
- Current mirrors with V3 onion addresses
- Real-time online/offline status for all links
- Response time metrics for mirror performance
- Reliability ratings and uptime statistics
- PGP verification information for link authenticity
- Step-by-step connection guide
- Copy-to-clipboard functionality
How to Connect: Step-by-Step Guide
Follow this guide to connect safely. Each step matters for maintaining security and anonymity when connecting through the Tor network.
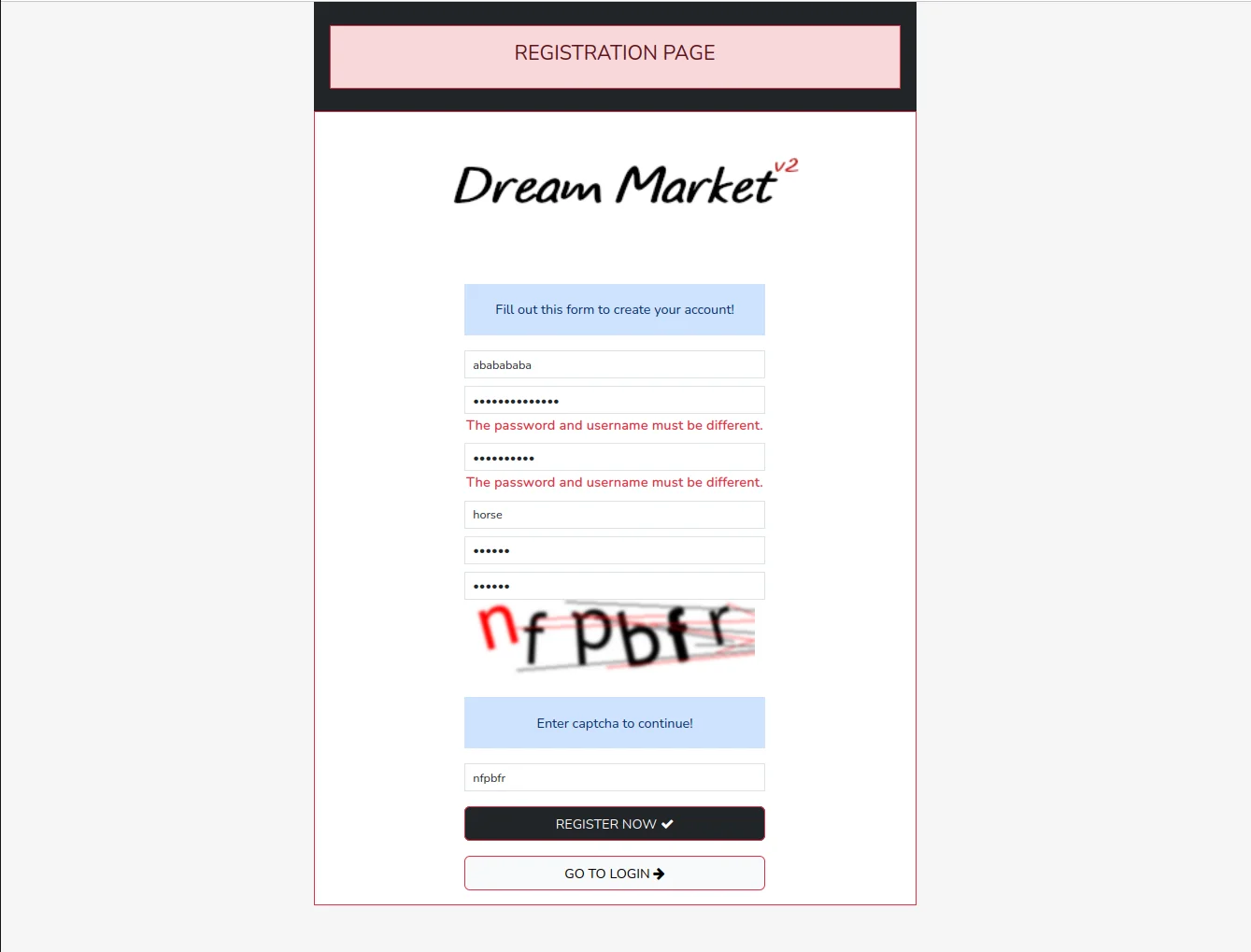
Download and Install Tor Browser
Access requires Tor Browser - the official gateway to .onion services. Download exclusively from the official Tor Project website. Never download from third-party sources as they may contain malware.
After downloading, verify the cryptographic signature of the installer to ensure authenticity. The Tor Project provides detailed verification instructions. This step prevents man-in-the-middle attacks.
Configure Tor Browser Security Settings
Before connecting, configure Tor Browser for maximum security. Navigate to Security Settings and set the level to "Safest" to disable JavaScript and other potentially dangerous features.
Additional security recommendations:
- Never maximize the Tor Browser window to prevent fingerprinting
- Disable any browser plugins or extensions
- Enable HTTPS-Only Mode for non-.onion sites
- Clear cookies and site data after each session
Copy Verified Link
Select an online mirror from the list above and click "Copy Link" to copy the complete onion URL to your clipboard. Links are 56-character V3 onion addresses providing strong cryptographic security.
Before using any link, verify it matches the official PGP-signed mirror list. URLs should never be obtained from search engines, forums with anonymous users, or unsolicited messages. Only use links from verified sources.
Connect to the Platform
Paste the copied link into the Tor Browser address bar. Double-check that the complete 56-character URL is correct before pressing Enter. The platform should load within 10-30 seconds depending on Tor network conditions.
If it doesn't load, try an alternative mirror from the list. Some mirrors may experience temporary downtime due to DDoS attacks or maintenance. The mirror infrastructure provides redundancy for continuous access.
Verify PGP Signature
Once connected, verify the platform's PGP signature before entering any credentials. A signed welcome message should be verified against the official PGP public key. This confirms you've connected to the authentic site and not a phishing page.
If the PGP signature doesn't verify correctly, immediately close the connection and try a different mirror. Phishing sites are common and designed to steal user credentials.
Bookmark Verified Mirrors
After successfully verifying a link, bookmark it in Tor Browser for future access. Bookmarks ensure you always return to verified mirrors. Update your bookmarks periodically as mirrors may change.
Never rely on browser history to find links, as this can be compromised. Always verify mirrors against current PGP-signed lists even when using bookmarks.
PGP Verification Guide
PGP verification authenticates links and communications. Signatures prove authenticity of official announcements, mirror lists, and platform messages. Understanding verification protects you from phishing and impersonation attacks.
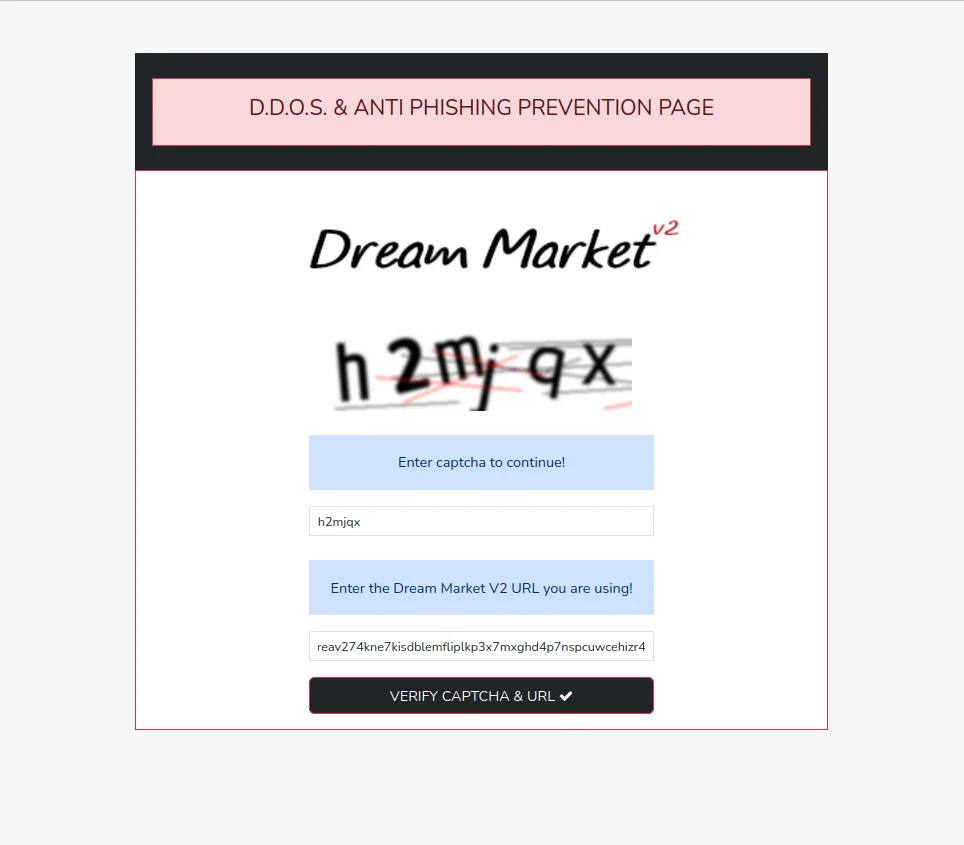
How to Verify Links with PGP
- Obtain Official PGP Key: Import the official public key from multiple independent sources
- Download Signed Mirror List: Administrators publish signed mirror lists with all official onion URLs
- Verify Signature: Use GPG to verify the signature on the mirror list
- Compare URLs: Ensure the link you're using appears in the verified list
- Check Fingerprint: Verify the PGP key fingerprint matches official records
PGP Verification Commands
# Import public key
gpg --import official_public.asc
# Verify signed mirror list
gpg --verify mirrors.sig mirrors.txt
# Check key fingerprint
gpg --fingerprint "Official Key"
Signs of Phishing Links
- URLs shorter than 56 characters (not V3 format)
- Missing or invalid PGP signature on welcome message
- Links from unverified sources like search engines or random forums
- Requests for login before interface loads
- Different appearance or layout than genuine site
- Unusual wallet addresses for deposits
- Spelling errors or strange formatting
- Requests to disable security features
Access Troubleshooting
Experiencing connection issues? This troubleshooting guide addresses common problems. Most issues can be resolved by following these steps.
Platform Not Loading
If a mirror isn't loading:
- Try alternative mirrors from the verified list above
- Request a new Tor circuit (Tor Browser menu → New Identity)
- Check if Tor Browser needs updating to latest version
- Wait 15-30 minutes - temporary issues happen
- Verify your internet connection is working properly
- Disable any VPN if running
- Try connecting from a different network
Loading Slowly
Slow access can be improved by:
- Selecting mirrors with lower response times
- Connecting during off-peak hours
- Requesting a new Tor circuit for potentially faster routes
- Ensuring no other applications are consuming bandwidth
- Closing unused browser tabs
Login Issues
If you cannot log in:
- Verify you're on an authentic mirror (check PGP signature)
- Ensure CAPS LOCK is off and credentials are entered correctly
- Complete 2FA verification if enabled on your account
- Use account recovery if you've lost credentials
- Try a different mirror - some may have caching issues
All Mirrors Offline
If all mirrors appear offline:
- Platform may be undergoing scheduled maintenance
- A major DDoS attack may be affecting infrastructure
- Check privacy news sources for status updates
- Return to this page later for updated mirror status
Operational Security (OPSEC)
Proper OPSEC protects your identity and prevents correlation attacks that could compromise anonymity. These practices apply to all darknet activity.
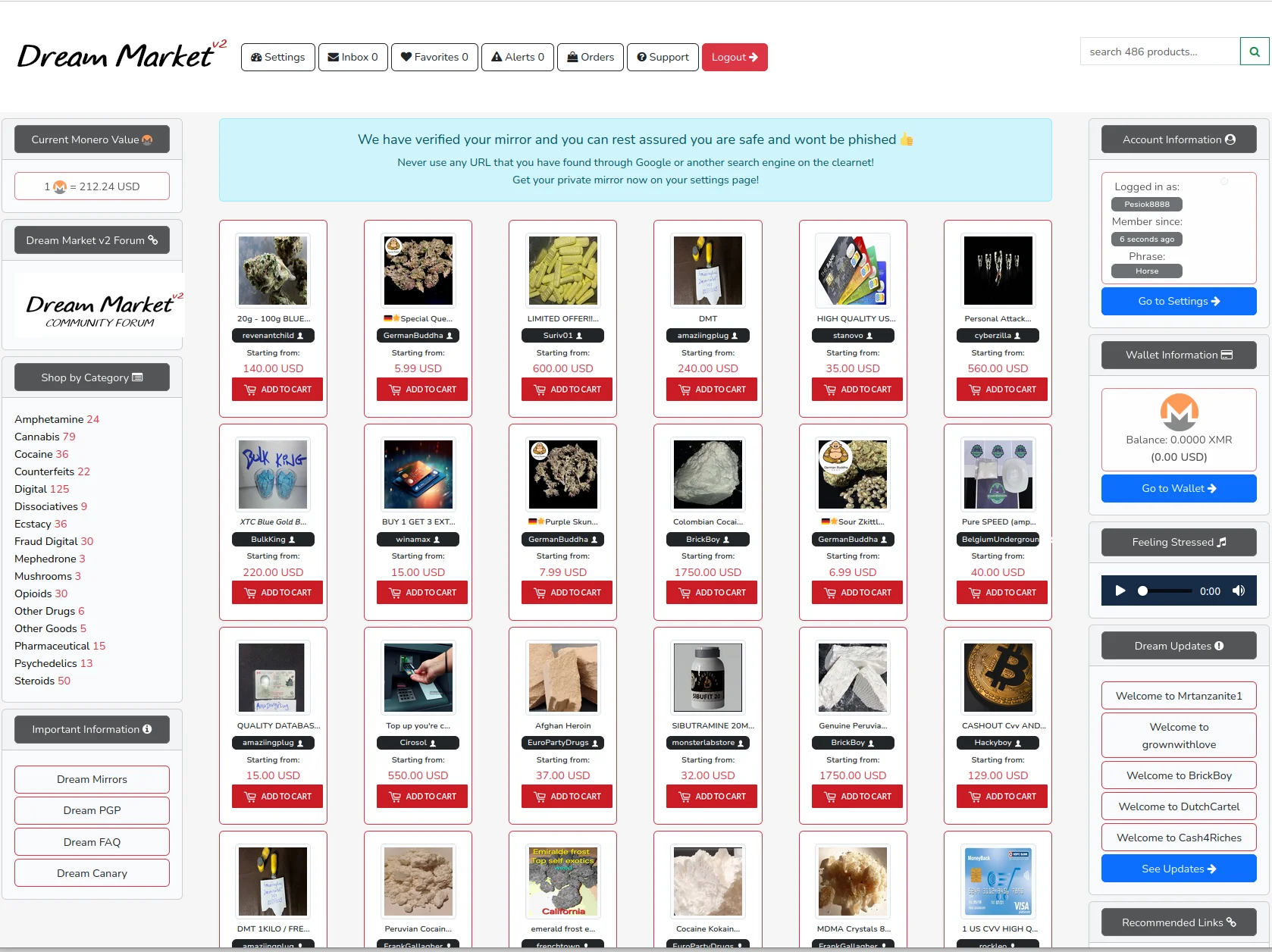
Before Connecting
- Consider using Tails OS for amnesia computing that leaves no traces
- Ensure your device has full-disk encryption enabled
- Close all other applications before opening Tor Browser
- Disconnect from any VPNs unless you understand the implications
- Use a dedicated device if possible
- Verify you're on a secure, trusted network
- Check for shoulder surfers in public spaces
During Sessions
- Never access personal accounts while session is active
- Don't download files to your main system
- Use KeePassXC for unique, strong passwords
- Encrypt all sensitive communications with PGP
- Avoid sharing personal information in messages
- Don't copy sensitive data to regular clipboard
- Monitor for unusual browser behavior
After Sessions
- Always click "New Identity" in Tor Browser after each session
- Clear all browser data and cache
- If using Tails, reboot to ensure all traces are cleared
- Don't discuss activities on social media or forums
- Wait before resuming normal internet activity
- Securely delete any temporary files
Understanding Connection Security
Every connection you make creates potential exposure points. Understanding how these work helps you minimize risk. When you connect through Tor, your traffic passes through three relays before reaching the destination. Each relay only sees one hop of the journey. The entry relay sees your real IP but not your destination. The exit relay sees the destination but not your IP. For .onion sites, there is no exit relay since the connection stays entirely within the Tor network.
This architecture provides strong anonymity but isn't foolproof. Timing correlation attacks could theoretically link your entry and exit points if an adversary controls both. Using the same circuit for extended periods increases exposure. That's why the "New Identity" function matters. It forces new circuit construction, breaking any accumulating correlations.
Network-level anonymity doesn't help if you reveal identity through behavior. Logging into personal accounts, using identifiable writing styles, or sharing information that narrows down your identity defeats technical protections. Security requires consistency across all layers. Think of anonymity as a chain where every link matters.
Security Resources
🕒 Page last updated: